Decentralization sets cryptocurrency apart from other assets, and MetaMask wallets play a crucial role in enabling users to manage their crypto assets in a decentralized manner. However, despite the benefits, there are potential risks associated with using MetaMask. As a smart investor, it’s essential to stay informed about your investments. In this guide, we will discuss MetaMask wallet security and provide tips on how to keep your funds safe.
Potential Risks While Using MetaMask
While using MetaMask, users might not be fully aware of several risks, especially given the newness of the technology and the rise in cyber scams. To ensure the safety and security of your digital assets, it’s crucial to be informed about the potential risks while using MetaMask:

Phishing Attacks:
Phishing attacks are a major threat to MetaMask users, where malicious actors attempt to trick users into revealing their private keys or sensitive information through fake websites or emails that mimic legitimate platforms.
Malicious Websites:
Visiting malicious websites poses a significant risk to MetaMask users. These sites may contain harmful scripts or malware designed to exploit browser vulnerabilities and compromise your wallet’s security.
Smart Contract Vulnerabilities:
Vulnerabilities in smart contracts can lead to the loss of funds or unauthorized access to your wallet. Always exercise caution when interacting with smart contracts.
Inadequate Security Measures:
While MetaMask provides several security features, ensuring the safety of your funds ultimately depends on the user. Poor security practices can expose your wallet to various threats. Always prioritize strong security measures to protect your assets.
MetaMask Security Features
MetaMask is continuously working to enhance wallet security. In this section, we will discuss the current security features of MetaMask that help you protect your digital assets.
- Encryption:
User configurations are stored on MetaMask servers and encrypted with a uniquely generated key that only the user possesses. This ensures that no one else can access these configurations.
- Blockaid:
MetaMask has partnered with Blockaid to offer a unique privacy feature that allows you to simulate transactions before signing them. This feature alerts you to potential scams and can help you avoid malicious websites. It is currently an opt-in feature.
- Secret Recovery Phrase:
Also known as a secret recovery phrase, MetaMask uses seed phrases to help users recover their wallets in case they forget or lose their passwords.

- Privacy Alerts:
MetaMask employs phishing detection to warn users about phishing domains targeting Ethereum users. This helps prevent users from falling victim to phishing attacks.
- Smart Contract Decoding:
MetaMask enhances user experience by customizing the activity tab with messages based on the smart contracts you interact with. It uses a service called 4byte.directory to decode data, providing a more readable version of the smart contract. This reduces the risk of approving malicious actions, though it may expose your IP address.
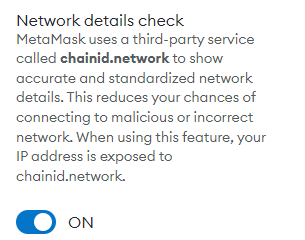
- Network Details
Check: MetaMask uses a third-party service called chainid.network to offer accurate and standardized network details. This minimizes the risk of connecting to malicious or incorrect networks, although it does expose your IP address to chainid.network.
How to Access MetaMask Security Features:
MetaMask wallet security features can be easily accessed through the MetaMask settings. Follow these steps:
Step 1: Open the MetaMask wallet extension in your browser.
![]()
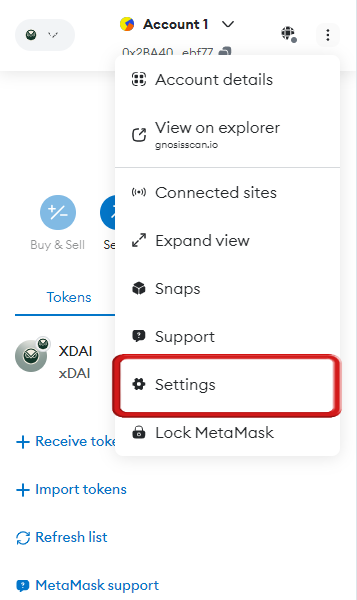
Step 2: Click on the “More options” icon in the top right corner.

Step 3: Select “Settings” from the menu.
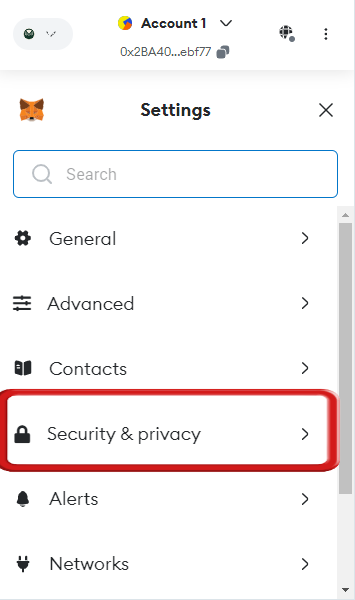
Step 4: From the settings menu, click on “Security & Privacy”.
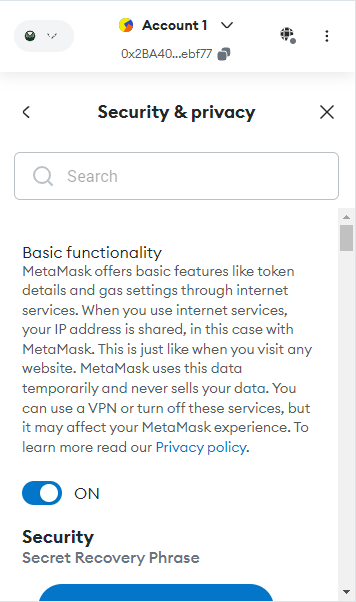
Step 5: Review the available security features to ensure your MetaMask wallet is secure.
Tips to Protect your MetaMask Wallet
To ensure the safety and security of your MetaMask wallet, it’s essential to implement robust security practices. Here are some comprehensive tips to help protect your MetaMask wallet:
1. Implement Strong Password Practices
- Create a Strong Password: Use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid easily guessable information like names or birth dates.
- Change Passwords Regularly: Regularly update your passwords to enhance security.
2. Update Browser & MetaMask
- Keep Software Up to Date: Regular updates to your browser and MetaMask extension address potential security risks and improve overall performance. Most modern browsers update automatically, but it’s good practice to manually check for updates periodically.
3. Be Cautious with dApps & Links
- Review Transactions Carefully: Always review transaction messages displayed by MetaMask before confirming any action. Watch out for unexpected requests for excessive gas fees or other suspicious activity.
- Avoid Unfamiliar Links: Be wary of clicking on unfamiliar links or downloading files from untrusted sources to prevent phishing attacks and malware infections.
4. Keep Your Recovery Phrase Secure
- Store Offline: Write your recovery phrase on paper and store it in a safe place. Avoid storing it digitally or sharing it with anyone.
- Never Share: Do not share your recovery phrase with anyone, even if they claim to be from MetaMask.
5. Connect Only to Trusted Websites
- Verify URLs: Always double-check the URL of the website you are connecting to, especially when interacting with Web3 applications and websites. Phishing websites can lead to loss of cryptocurrency.
6. Use Multiple MetaMask Wallets
- Distribute Assets: If you own valuable NFTs or significant amounts of cryptocurrency, consider distributing them across multiple wallets. Using a hardware wallet like Ledger adds an extra layer of security.
Potential Scams
Over the years, MetaMask users have encountered various scam attempts. While some scams are obvious, others are well disguised and harder to detect. We will explore a range of potential scams, how they are disguised, and how users can identify them.
| Scam | How to Detect |
|---|---|
| Signature Phishing | Verify dapp legitimacy, check URLs carefully, and manage permissions regularly |
| Airdrop Scams | Be cautious of third-party sites asking for sensitive information |
| Verification Email Scam | Look closely at the sender’s email address and URL |
| Address Poisoning | Double-check the complete address |
Signature Phishing Scam
Off-chain signatures allow users to authenticate actions without broadcasting them to the network, making them susceptible to misuse.
How it works:
- Scammers create fraudulent decentralized applications (dApps) to attract users.
- These dApps prompt users to sign off-chain messages, often disguised as harmless actions like depositing tokens or listing NFTs.
- The scammer uses the signed message to steal assets, such as giving unlimited token approval or listing all NFTs in the user’s account.
- Examples of Signature phishing are NFT Signature Phishing and Permit2 Signature Phishing.
Always verify the legitimacy of dApps and URLs before signing any messages, and regularly manage your permissions to minimize risks.
Airdrops Scams
Airdrop scams involve token creators sending free tokens to Ethereum addresses. Scammers exploit this by tricking users into revealing sensitive information or giving permission to access their wallets.
How it works:
- A user notices new, unexpected tokens in their wallet.
- Curious, they attempt to swap these tokens for ETH on a token swap site.
- The swap fails, and the user is redirected to a third-party site.
- On this site, they might be phished into entering their Secret Recovery Phrase, giving scammers control over their wallet.
- Alternatively, they might unknowingly grant permission for the site to take their tokens instead of receiving any.
Always be cautious with unexpected tokens and avoid interacting with unfamiliar third-party sites.
Verification Email Scam
Verification email scams involve fake emails claiming to be from MetaMask, asking you to verify or update your account, prove your identity (KYC), or click a button or link. These emails are scams.
How it works:
- You receive an email claiming to be from MetaMask, asking for account verification or updates.
- The email threatens to block your MetaMask account if you don’t comply.
Always verify the authenticity of such emails by checking MetaMask’s official channels and never click on suspicious links.
Address Poisoning Scam
Address poisoning scams target user transaction addresses on MetaMask. When you send or receive crypto, the transaction appears in your list, showing a shortened form of the third-party address.
How it works:
- A scammer creates an address similar to your recent transactions using vanity address generators.
- They send you a small amount, making their address appear in your transaction list.
- Since the address looks similar, you might mistakenly select it and transfer your cryptocurrency to the scammer’s wallet.
To avoid falling victim to address poisoning, develop a habit of carefully verifying the full address every time you make a transaction, regardless of how familiar it may seem.
General Best Practices
- Never Share Private Keys: Keep your private keys to yourself; do not share them with anyone, including MetaMask support or exchanges.
- Bookmark Correct URLs: Always bookmark the correct URLs for dApps and avoid clicking on links from unknown sources.
- Minimize Large Holdings in MetaMask: Treat MetaMask as a wallet, not a bank. Avoid keeping large sums in it.
- Discuss Crypto, Not Holdings: Avoid revealing how much cryptocurrency you hold to prevent becoming a target.
- Avoid Clicking on Crypto Ads: Be cautious with crypto ads as scammers often use them to get ahead of real protocols in search results.
- Securely Store Private Keys: Never save private keys on your computer or phone. Write them down on paper and keep them safe.
- Memorize Private Keys: If possible, memorize your private keys for an added layer of security.
- Use Reputable Exchanges: To enhance the security of your MetaMask wallet and manage your crypto assets, consider using reputable exchanges like Binance and MEXC.
Bottomline
Securing MetaMask wallet requires vigilance, proactive measures, and continuous education about potential risks and scams. By adhering to best practices, utilizing MetaMask’s built-in security features, and remaining cautious when interacting with dApps and third-party services, MetaMask users can significantly enhance the safety of their crypto assets. Remember, cybercrime is quite common and can sometimes be difficult to trace, so staying informed and cautious is key to safeguarding your investments.
FAQs
1. Are my transactions private when using MetaMask?
MetaMask itself does not collect sensitive information about your transactions. However, blockchain transactions are inherently public and visible to anyone. If maintaining privacy is a major concern, consider using privacy-focused cryptocurrencies or additional tools like VPNs to enhance your anonymity.
2. What steps should I take if my MetaMask account is compromised?
If you suspect that your MetaMask account has been compromised or you lose access to it, take immediate action. Disconnect any linked accounts or devices, change your passwords, and contact MetaMask support for assistance. Additionally, report the incident to relevant authorities if necessary.
3. How can I ensure the safety of third-party dApps connected through MetaMask?
While many dApps connected through MetaMask are reliable, it’s important to be cautious. Conduct thorough research on any third-party application before using it and stay vigilant for potential scams or malicious activities. Always verify the authenticity of the dApp and be mindful of the permissions you grant.















